Inside the Microsoft Breach by Midnight Blizzard
A recent cybersecurity breach at Microsoft has cast a spotlight on the relentless and sophisticated threats that pervade our digital ecosystem.
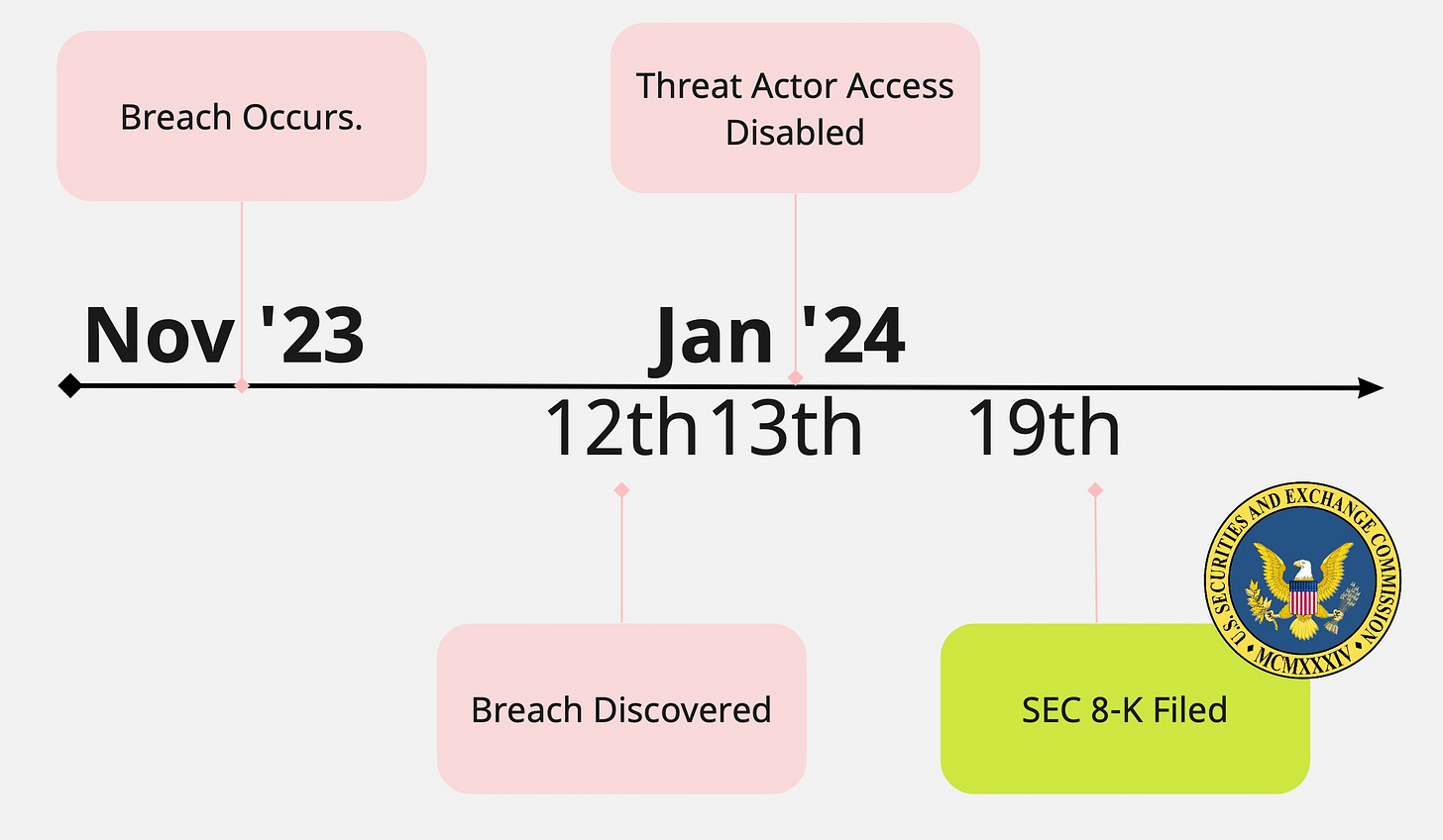
The Breach Timeline Revealed
In a disconcerting revelation, it was uncovered that in late November 2023, nation state threat actors managed to pierce through Microsoft's defenses. This breach, however, remained undetected until 12th January 2024, unveiling a gap in the tech giant's security apparatus. Microsoft moved swiftly to disable access for the threat actor on 13th January 20024. The assailants, identified as the Russian state-sponsored group Midnight Blizzard (also known as Nobelium), orchestrated this complex cyber intrusion.
Microsoft filed an 8-K with the Securities and Exchange Commission (SEC) on January 19, 2024. This disclosure brought to light the meticulous and prolonged nature of the cyberattack, though Microsoft assured there was no material impact yet from the breach.
Decoding Midnight Blizzard's Tactics
The breach was initiated with a password spray attack, a technique that allowed the perpetrators to infiltrate a test tenant. Through a series of calculated steps, they then managed to compromise the email accounts of senior leadership, demonstrating the perilous potential of lateral movement within cybersecurity breaches.
The Anatomy of a Password Spray Attack
Password spraying stands as a stark reminder of the importance of robust security protocols, particularly Multi-Factor Authentication (MFA). This method of attack, by its nature, bypasses traditional security measures, allowing for widespread unauthorized access under certain conditions.
Detecting Password Spraying
Detecting password spray attacks requires a multifaceted approach that combines technology, vigilance, and strategic deception.
Use Deception Techniques:
Creating decoy accounts, or honey accounts, that are monitored but not associated with real users, can serve as an early warning system for password spray attacks. Any login attempt on these accounts is a clear indication of a malicious actor, as these credentials should never be used legitimately
Implement Anomaly Detection Algorithms:
By utilizing machine learning algorithms, organizations can analyze login attempts and identify patterns that deviate from the norm. An anomaly detection system can flag unusual login attempts, such as repeated failures from a cluster of IP addresses targeting multiple accounts, which is indicative of a password spray attack. However, in this case Midnight Blizzard's strategy involved the use of residential proxy networks. This approach allowed them to route their malicious traffic through a myriad of IP addresses indistinguishable from those used by legitimate users. Such tactics complicate detection methods based on indicators of compromise (IOC), as the rapid turnover of IP addresses masks the attack's origin effectively.
Lateral Movement: The Silent Threat
A deeper dive into the cybersecurity breach that rattled Microsoft reveals the clever and cunning strategies employed by Midnight Blizzard to navigate through the company's defenses. Central to their approach was the exploitation of OAuth applications, a tactic that underscores the sophistication of modern cyber threats.
Midnight Blizzard's modus operandi involved compromising user accounts to create, modify, and grant extensive permissions to OAuth applications under their control. This manipulation of OAuth applications not only facilitated the concealment of malicious activities but also ensured persistent access within applications, irrespective of the initial account's security status.
The threat actors leveraged their initial breach to identify and compromise a legacy test OAuth application, which had elevated access privileges within the Microsoft corporate environment. This step was crucial, as it allowed them to create additional malicious OAuth applications and establish a new user account specifically to grant consent for these applications within Microsoft's corporate ecosystem.
By exploiting the legacy test OAuth application, Midnight Blizzard awarded themselves the "full_access_as_app" role in Office 365 Exchange Online, a move that effectively opened the door to accessing mailboxes at will. This capability was then used to authenticate to Microsoft Exchange Online, targeting corporate email accounts directly.
Assessing the Impact
Despite the breach's apparent containment, with Microsoft asserting no material impact on its operations as of the filing date, the long-term implications remain a subject of scrutiny. The breach's revelation underscores the paramount importance of vigilance and continuous improvement in cybersecurity measures.
A Leader's Perspective
CrowdStrike CEO George Kurtz's insights on the breach emphasize the cunning of Nobelium and the critical need for industry-wide collaboration and transparency in cybersecurity efforts.
Source: CNBC
Lessons for the Future
This breach serves as a clarion call for the adoption of Multi-Factor Authentication, the importance of segregating test and production environments, and the necessity of a zero-trust security model to mitigate the risk of similar incidents.
The Attack Unfolded
Detailed analysis provided by Microsoft sheds light on Midnight Blizzard's sophisticated methods, from targeted password spraying to the exploitation of legacy systems, offering crucial insights into defending against such multifaceted cyber threats.